Under Attack?
Broken Network System?
Leave your details below and we’ll get back to you shortly
This blog post explores the critical challenges in maintaining IP-to-user mapping when migrating Active Directory to the cloud, and details an innovative solution using Juniper Mist NAC, AWS services, and API integration with corporate firewalls. Organizations transitioning to cloud-based identity services often face significant gaps in user attribution and security policy enforcement that require creative architectural approaches to resolve.
The Challenge: IP-to-User Mapping in a Cloud-First World
Understanding the Problem
When organizations migrate their on-prem AD to cloud environment, one of the most significant challenges they face is maintaining accurate IP-to-user mapping. Traditionally, on-prem AD servers provide this critical mapping through authentication processes, allowing network security teams to identify which users are using which IP addresses at any given time. This mapping forms the foundation for:
In on-prem environments, domain controllers track user logins, and network security devices like firewalls can query this information directly or receive it through agents. However, when AD moves to the cloud, this direct communication path often breaks, creating significant visibility gaps for security teams.
Impact on Network Security Enforcement
Without accurate IP-to-user mapping, organizations face several critical security challenges:
Network security is fundamentally about maintaining visibility and control over who accesses what resources. When user identity information is lost, security teams must rely solely on IP addresses, which are insufficient for modern zero-trust security models. The consequences include:
These challenges are particularly acute in organizations that have invested heavily in identity-based security controls, as the migration to cloud-based identity services can unintentionally undermine these investments.
Looking for other reliable sources
Organizations can leverage several reliable methods to maintain IP-to-user mapping. Below are the most common approaches, each with distinct advantages and use cases:
1.Always On VPN Solutions
Modern Always On VPN implementations provide persistent connectivity and user attribution through authentication logs. This approach is ideal for organizations with remote users requiring secure, identity-based access to cloud resources. This solution integrates seamlessly with SASE architectures.
2. Captive Portal Authentication
Systems like Palo Alto’s Captive Portal enforce user authentication before network access:
Captive portals are particularly effective for guest networks or environments with unmanaged devices.
3.Syslog-Based User-ID Mapping
Firewalls like Palo Alto Networks and FortiGate (with the help of FortiAuthenticator) can ingest authentication logs to build IP-user mappings:
This method suits organizations with existing SIEM or log aggregation infrastructure.
4. API-Driven Integration
Custom integrations using vendor APIs enable real-time user mapping updates:
API-based approaches offer maximum flexibility for organizations with bespoke authentication workflows.
Key Considerations for Implementation
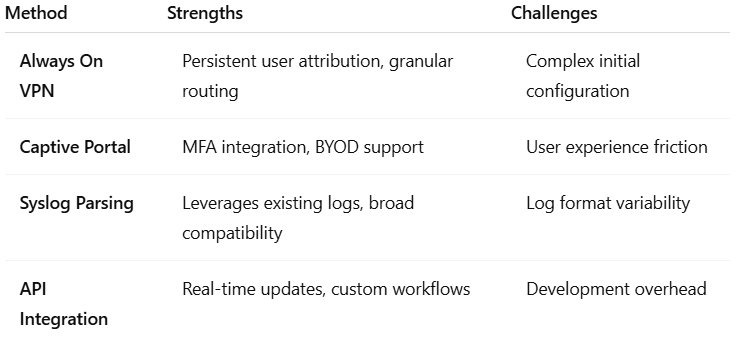
Organizations should evaluate these options based on their existing infrastructure, security requirements, and cloud adoption stage. Hybrid approaches (e.g., combining syslog parsing with API-driven updates) often provide the most resilient solution.
Our Custom Solution Architecture
Overview
To address the IP-to-user mapping challenge in our environment, we developed a custom solution that leverages:
This architecture provides a scalable, cost-effective solution that maintains accurate IP-to-user mapping without the need for additional commercial software licenses.
Component Breakdown
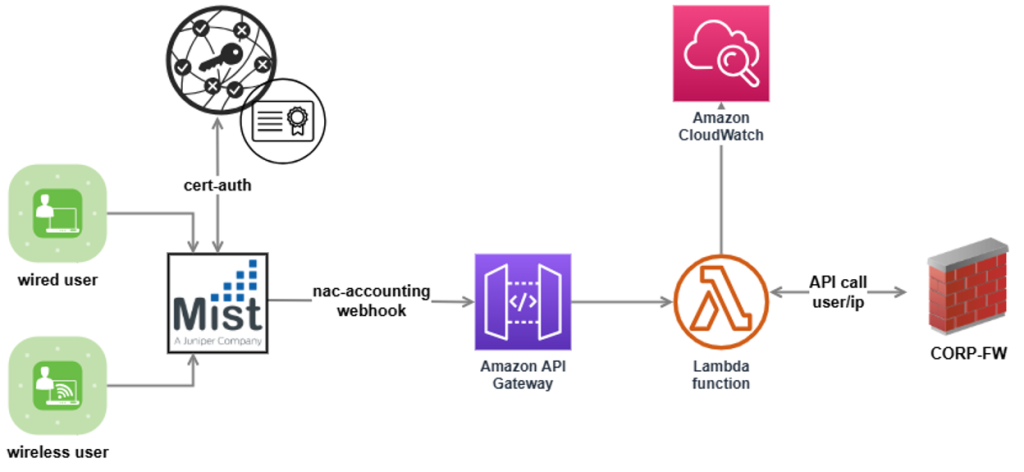
Juniper Mist NAC
Juniper Mist Access Assurance serves as the foundation of our solution, providing authentication services and detailed accounting logs. The cloud-based nature of this service aligns with our cloud-first strategy while eliminating the need to maintain on-premises authentication servers, it relies on RadSec (RADIUS over TLS) to secure communications between network devices and the cloud authentication service.
Key features we leverage include:
AWS API Gateway and Lambda
The AWS components of our solution serve as the integration layer:
Our Lambda function parses the accounting logs, extracting username, IP address, timestamp, and other relevant attributes. It then formats this information for consumption by our corporate firewall.
Firewall Integration
The final component of our solution is the integration with our corporate firewall through its API. The Lambda function makes API calls to update the user-ID mapping table on the firewall, ensuring that security policies can be accurately applied based on user identity rather than just IP address.
Results and Benefits
Implementing our custom solution has yielded several significant benefits:
Improved Security Posture
By maintaining accurate IP-to-user mapping, we’ve strengthened our security posture in several ways:
Operational Efficiency
The solution has also improved our operational efficiency:
Cost Savings
By leveraging already existing tools and licenses with the addition of cloud-based flexibility we were able to deliver the solution with minimal cost:
Conclusion
Migrating Active Directory to the cloud creates significant challenges for maintaining IP-to-user mapping, but creative solutions can bridge this gap effectively. Our approach, leveraging Juniper Mist NAC, AWS services, and API integration, demonstrates that organizations can maintain robust security controls even during major infrastructure transitions.
By thinking beyond traditional solutions and embracing cloud-native integration approaches, we’ve developed a system that improves our security posture, enhances operational efficiency, and reduces costs. This architecture serves as a model for addressing similar challenges in cloud-first environments.
For organizations facing similar challenges, we recommend:
With proper planning and implementation, the challenge of IP-to-user mapping without on-prem AD can be effectively addressed, maintaining the security foundation needed for modern zero-trust security architectures.
System Architect

Leave your details below and we’ll get back to you shortly